Microsoft Defender for Endpoint, the new name for Microsoft Defender Advanced Threat Protection, is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats.
Microsoft Defender for Endpoint comes with the Windows 10 E5/A5 and Microsoft 365 E5/A5 Licences. It requires Microsoft Defender Antivirus as the primary antimalware product on your devices or Microsoft Defender Antivirus Early Launch Antimalware (ELAM) driver to be enabled on the device.
Microsoft Defender for Endpoint security solution comprises of:
Endpoint behavioral sensors that collect and process behavioral signals from the operating system and send this sensor data to your organisation’s private, isolated, cloud instance of Microsoft Defender for Endpoint.
Cloud security analytics that leverage big-data, device-learning, and unique Microsoft optics across the Windows ecosystem, enterprise cloud products (such as Office 365), and online assets. Behavioral signals are translated into insights, detections, and recommended responses to advanced threats.
Threat intelligence that is generated by Microsoft hunters, security teams, and augmented by threat intelligence provided by partners. Threat intelligence enables Defender for Endpoint to identify attacker tools, techniques, and procedures, and generate alerts when they are observed in collected sensor data.
Microsoft Defender for Endpoint demonstrated industry-leading optics and detection capabilities in the recent MITRE evaluation.
Deployment
The organisations global administrator or Security administrator should navigate to https://securitycenter.windows.com.
During the first time, a Welcome screen is shown, and the administrator should follow the wizard to go through the authorization steps, set up preferences such as Data storage location and Data retention policy, and finally create your organizations cloud instance for Microsoft Defender for Endpoint. If the organization requires the endpoints to use a Proxy to access the Internet, configure the network manually for static proxy server, or auto-discover if Transparent proxy or Web Proxy Autodiscovery Protocol (WPAD) is implemented in the network topology.
Onboarding Devices can be done through a script specific to the device’s Operating system, which can be downloaded from the security center website, and run natively on the device. For larger scale onboarding or centralized, automated onboarding of devices in a production environment the deployment package can be pushed to the endpoint devices through a group policy or a configuration manager. For onboarding mobile devices (IOS/Android), the company’s existing mobile device management solution such as Intune can be used. The MDM company portal app should be downloaded to the device and the mobile device registered to it. The Microsoft Defender for Endpoint app would also be needed to be installed as the Antivirus agent in the mobile device.
Dashboard
From the dashboard at https://securitycenter.windows.com, you can access the incidents, device list, active automated investigations, active alerts, alerts queue, automated investigations statistics, devices at risk, users at risk, devices with sensor issues, service health, detection sources, and daily devices reporting dashboards.
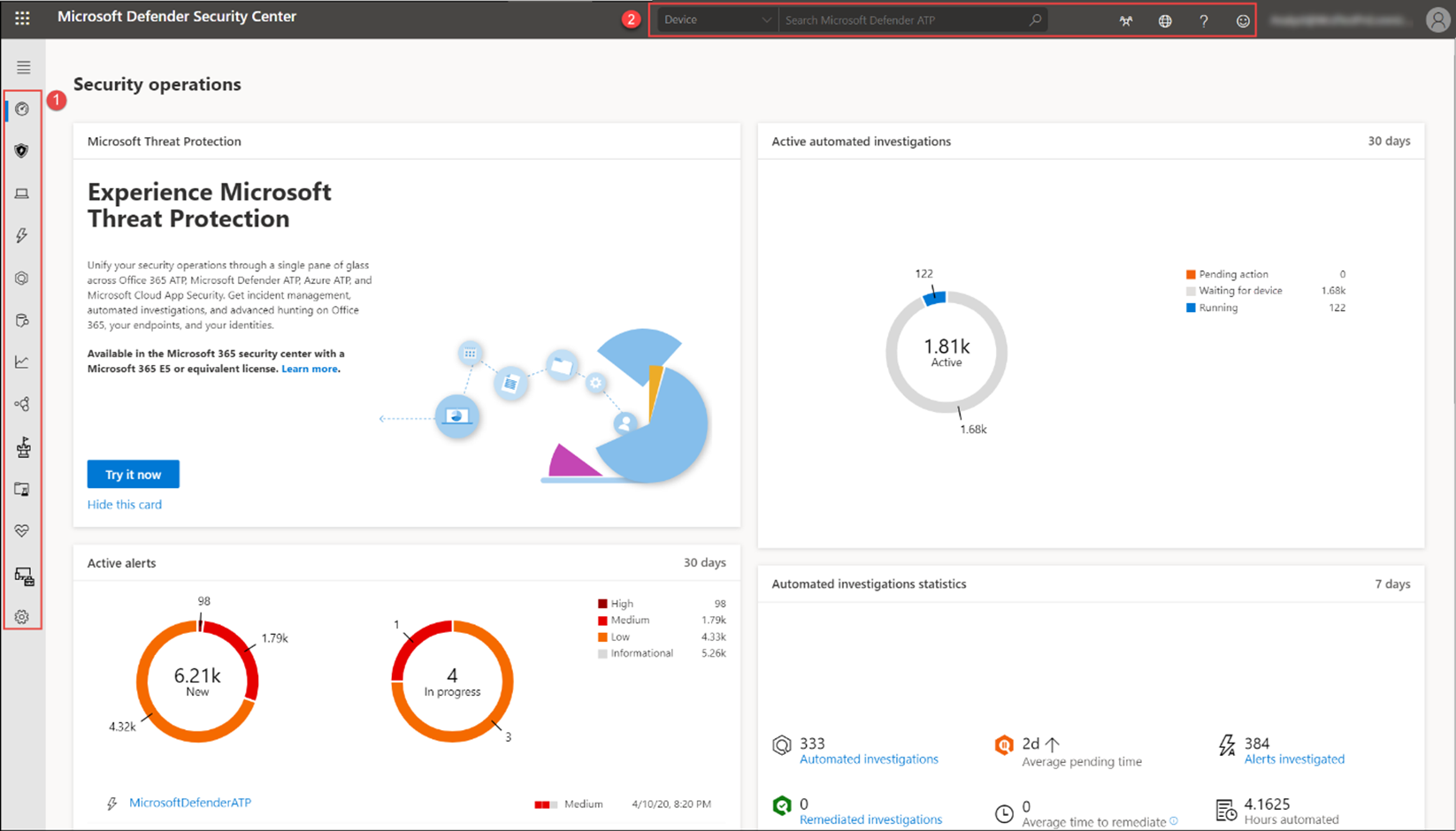
Automated investigations tab displays automated investigations that have been conducted in the network, triggering alert, the status of each investigation and other details such as when the investigation started and the duration of the investigation.
Advanced hunting allows you to proactively hunt and investigate across your organization using a powerful AI based search, optimization and query engine.
Partners & APIs tab help you to view supported partner connections, which enhance the detection, investigation, and threat intelligence capabilities of the platform. You can also view connected applications, the API explorer, API usage overview, and data export settings.
Evaluation and tutorials allow you to manage test devices, attack simulations, and reports. You can learn and experience the Defender for Endpoint capabilities through a guided walk-through in a trial environment.
Threat simulator scenarios can be performed in a lab setup by adding up to 4 test devices in a sandbox environment, and creating attack simulations and testing their remediation steps. From the Evaluation and tutorials tab go to Simulation & tutorials, then select Simulations catalogue. A list of supported third-party threat simulation agents are listed, each simulation comes with an in-depth description of the attack scenario and references such as the MITRE attack techniques used and sample Advanced hunting queries you can run. You can walk through the lab progress bar and explore the automated investigation and remediation.
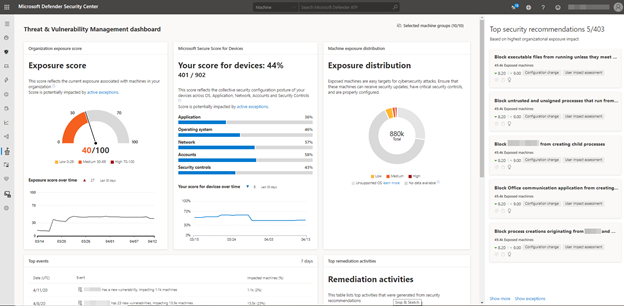
Threat & Vulnerability Management
Threat & Vulnerability Management (TVM) Threat & Vulnerability Management is a component of Microsoft Defender for Endpoint, and provides both security administrators and security operations teams with unique value, including:
Real-time endpoint detection and response (EDR) insights correlated with endpoint vulnerabilities.
Invaluable device vulnerability context during incident investigations.
Built-in remediation processes through Microsoft Intune and Microsoft System Center Configuration Manager.
Attack surface reduction
Reducing the attack surface is the first line of defense in the security stack. By ensuring configuration and control rules settings are properly set and exploit mitigation techniques are applied, these set of capabilities resist attacks and exploitation. This set of capabilities includes:
Hardware-based isolation – Protect and maintain the integrity of a system as it starts and while it is running. Validate system integrity through local and remote attestation. And, use container isolation for Microsoft Edge to help guard against malicious websites.
Application control – Use application control so that your applications must earn trust in order to run.
Exploit protection – Help protect operating systems and apps your organization uses from being exploited. Exploit protection also works with third-party antivirus solutions.
Network protection – Extend protection to your network traffic and connectivity on your organization’s devices. (Requires Microsoft Defender Antivirus)
Web protection – Secure your devices against web threats and help you regulate unwanted content.
Controlled folder access – Help prevent malicious or suspicious apps (including file-encrypting ransomware malware) from making changes to files in your key system folders (Requires Microsoft Defender Antivirus)
Network firewall – Prevent unauthorized traffic from flowing to or from your organization’s devices with two-way network traffic filtering.
Next-generation protection
Microsoft Defender Antivirus is a built-in antimalware solution that provides next-generation protection for desktops, portable computers, and servers. Microsoft Defender Antivirus includes:
Cloud-delivered protection for near-instant detection and blocking of new and emerging threats. Along with machine learning and the Intelligent Security Graph, cloud-delivered protection is part of the next-gen technologies that power Microsoft Defender Antivirus.
Always-on scanning using advanced file and process behavior monitoring and other heuristics (also known as “real-time protection”).
Dedicated protection updates based on machine-learning, human and automated big-data analysis, and in-depth threat resistance research.
Endpoint detection and response
Microsoft Defender for Endpoint’s endpoint detection and response capabilities provide advanced attack detections that are near real-time and actionable. Security analysts can prioritize alerts effectively, gain visibility into the full scope of a breach, and take response actions to remediate threats. Inspired by the “assume breach” mindset, Defender for Endpoint continuously collects behavioral cyber telemetry. This includes process information, network activities, deep optics into the kernel and memory manager, user login activities, registry and file system changes, and other attack vectors.
Some of the response actions that can be used on endpoint devices include initiating an automated investigation or initiate live response session which gives you capability to access a device by using a remote shell connection on authorization and enabling you to collect forensic data, run scripts, send suspicious entities for analysis, remediate threats, and proactively hunt for emerging threats.
Other steps include running antivirus scan, restricting app execution, isolating devices, stopping, blocking and Quarantining files or processes, and consulting a threat expert.
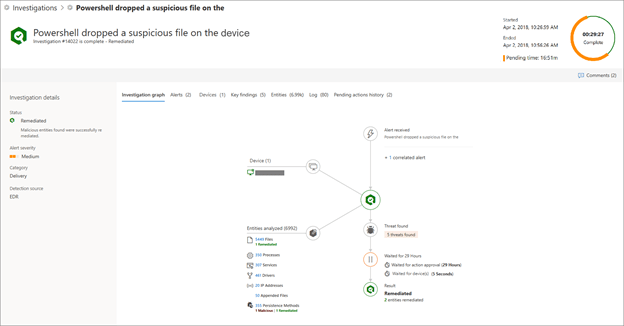
Automated investigation and remediation
The technology in automated investigation uses various inspection algorithms and is based on processes that are used by security analysts. AIR capabilities are designed to examine alerts and take immediate action based on the automation levels set where remediation and mitigation steps may or may not require approval to resolve breaches. AIR capabilities significantly reduce alert volume, allowing security operations to focus on more sophisticated threats and other high-value initiatives. The Action center keeps track of all the investigations that were initiated automatically, along with details, such as investigation status, detection source, and any pending or completed actions.
Microsoft Secure Score for Devices
As a part of the ‘Zero Trust’ approach to security, Microsoft 365 security products and services examine and rate the security posture of your organization with a secure score that helps assess the preparedness and capabilities of an organisation to handle breaches and fill their control gaps. Defender for Endpoint includes Microsoft Secure Score for Devices to help you dynamically assess the security state of your enterprise network, identify unprotected systems, and take recommended actions to improve the overall security of your organization.
Microsoft Threat Experts
Microsoft Defender for Endpoint’s new managed threat hunting service provides proactive hunting, prioritization, and additional context and insights that further empower Security operation centers (SOCs) to identify and respond to threats quickly and accurately. Defender for Endpoint customers can apply for the Microsoft Threat Experts managed threat hunting service to get proactive Targeted Attack Notifications and to collaborate with experts on demand.
Integration with Microsoft solutions
With Microsoft 365 Defender, Defender for Endpoint and various Microsoft security solutions form a unified pre- and post-breach enterprise defense suite that natively integrates across endpoint, identity, email, and applications to detect, prevent, investigate, and automatically respond to sophisticated attacks. The Microsoft security solutions that can be integrated with Defender for Endpoint include:
Azure Security Center
Azure Sentinel
Intune
Microsoft Cloud App Security
Microsoft Defender for Identity
Microsoft Defender for Office 365
